Dragonfly hackers target power grids
The Dragonfly group has been operating since 2011, says security firm Symantec, but has started a new campaign in recent months that could be a prelude to disruption.
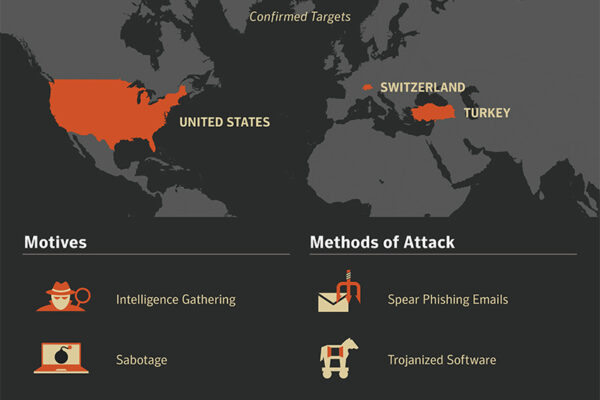
The group appears to be interested in both learning how energy facilities operate and also gaining access to operational systems themselves, says Symantec. This is particularly strong in the US, Turkey and Switzerland, using a range of techniques from malicious ‘phishing’ emails to Trojans. As well as sending malicious emails, the attackers also used watering hole attacks to harvest network credentials by compromising websites that were likely to be visited by those involved in the energy sector.
The stolen credentials were then used in follow-up attacks against the target organizations. Symantec also has evidence to suggest that files masquerading as Flash updates may be used to install malicious backdoors onto target networks.
It can be hard to attribute attacks to any one particular group, but the Heriplor and Karagany Trojans used in Dragonfly 2.0 were both also used in the earlier Dragonfly campaigns between 2011 and 2014.
Trojan.Heriplor is a backdoor that appears to be exclusively used by Dragonfly, and is one of the strongest indications that the group that targeted power operators between 2011 and 2014 is the same group that is behind the more recent attacks. This custom malware is not available on the black market, and has not been observed being used by any other known attack groups. It has only ever been seen being used in attacks against targets in the energy sector.
Symantec predicts that this intelligence gathering phase is a prelude to sabotage attacks, with the Dragonfly 2.0 campaign potentially providing access to operational systems that could be used for more disruptive purposes in future.
Dragonfly relies heavily on stolen credentials to compromise a network, so Symantec stresses the use of strong passwords that are at least 8-10 characters long (and preferably longer) and include a mixture of letters and numbers. Multiple, overlapping, and mutually supportive defensive systems should be used to guard against single point failures in any specific technology or protection method, including regularly updated firewalls as well as gateway antivirus, intrusion detection or protection systems (IPS), website vulnerability with malware protection, and web security gateway solutions throughout the network.
More details on the malware are at www.symantec.com
 If you enjoyed this article, you will like the following ones: don't miss them by subscribing to :
eeNews on Google News
If you enjoyed this article, you will like the following ones: don't miss them by subscribing to :
eeNews on Google News